We are close to the end of this guidance toward building the blue team home lab. Last time we configured a web server that is hosting a website, and a database, MariaDB. I’ve made some changes in the previous article so be sure to check them before continuing on this one.
This time we will focus on creating a bandito network or better say, simulate the external network, where our external threats are coming from. That network will contain a Kali Linux machine witch at some point in this guidance, we will use to simulate some attacks and detect them with our SIEM. So let’s get started.
Installation and configuration
First, download the Kali Linux VM that suits your need. In my case, it is a VMware machine.
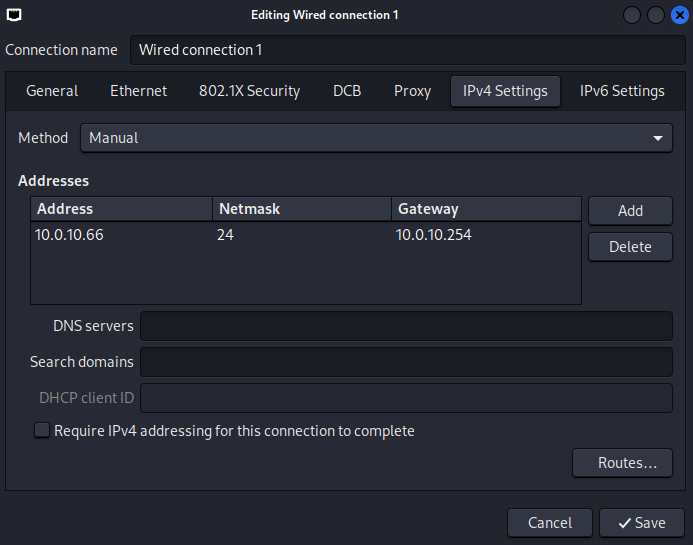
Once downloaded you can simply import the VM into your VMware or VirtualBox and leave the configuration settings default. It should be for a start in either NAT or Bridge mode when it comes to the network. Once done, power up the machine and log in. We will first perform some basic updates and upgrades with the commands sudo apt update and sudo apt upgrade.
Once all updates and upgrades are done, reboot the machine and after reboot, shut it down.
Network
Now we will configure our bandito machine to be in a Fake WAN network, which is just a simulation of the Internet, to be sure our machine does not have Internet access so we can avoid any chances to somehow some accident or magic, send attack toward some real-life environment.
In VMware/VirtualBox VM configuration, change the network adapter to the VLAN 10 (in my case) and then start the VM.
At this point, we will create a snapshot of our VM to have it always as a backup in case something breaks.
Firewall configuration
In theory, with the current network setup, our Bandit is coming from an “internal” network or sort of. In reality, there would be many different IP addresses, firewalls, routers, and other devices in between. But as we are just trying to create a “simple” lab, we are simulating and imagining that Bandito is coming from the external network. :)
So now we have our Kali Linux machine ready for some hacking. Now let’s make some additional changes to a firewall, to allow access to internal resources from the outside, like HTTP, SSH, and MySQL.
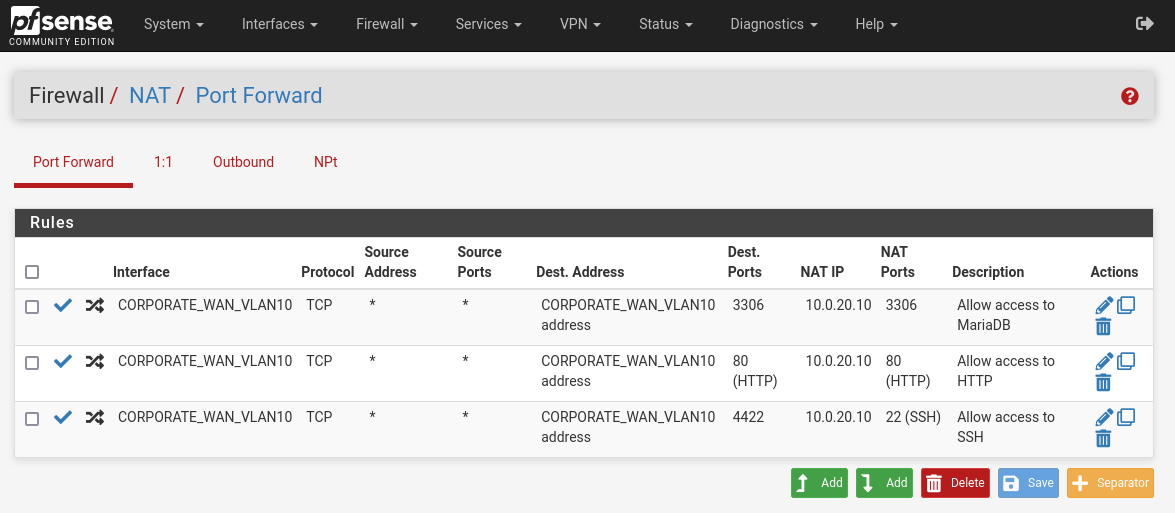
Start your firewall, log in, and go to Firewall > NAT > Port Forward menu. Then you need to create the rules like in the picture below. So we have any traffic coming on our WAN VLAN 10 interface on ports 80, 3306, and 4422, redirect/NAT toward our Linux server IP, 10.0.20.10 on ports 3306, 80, and 4422, respectively. If you wonder why 4422, sometimes people want to allow SSH publicly but on a different port. They believe that is a security measure, but well…it is not.
Test connectivity
Now for the final part let’s test connectivity from Kali Linux toward the internal network.
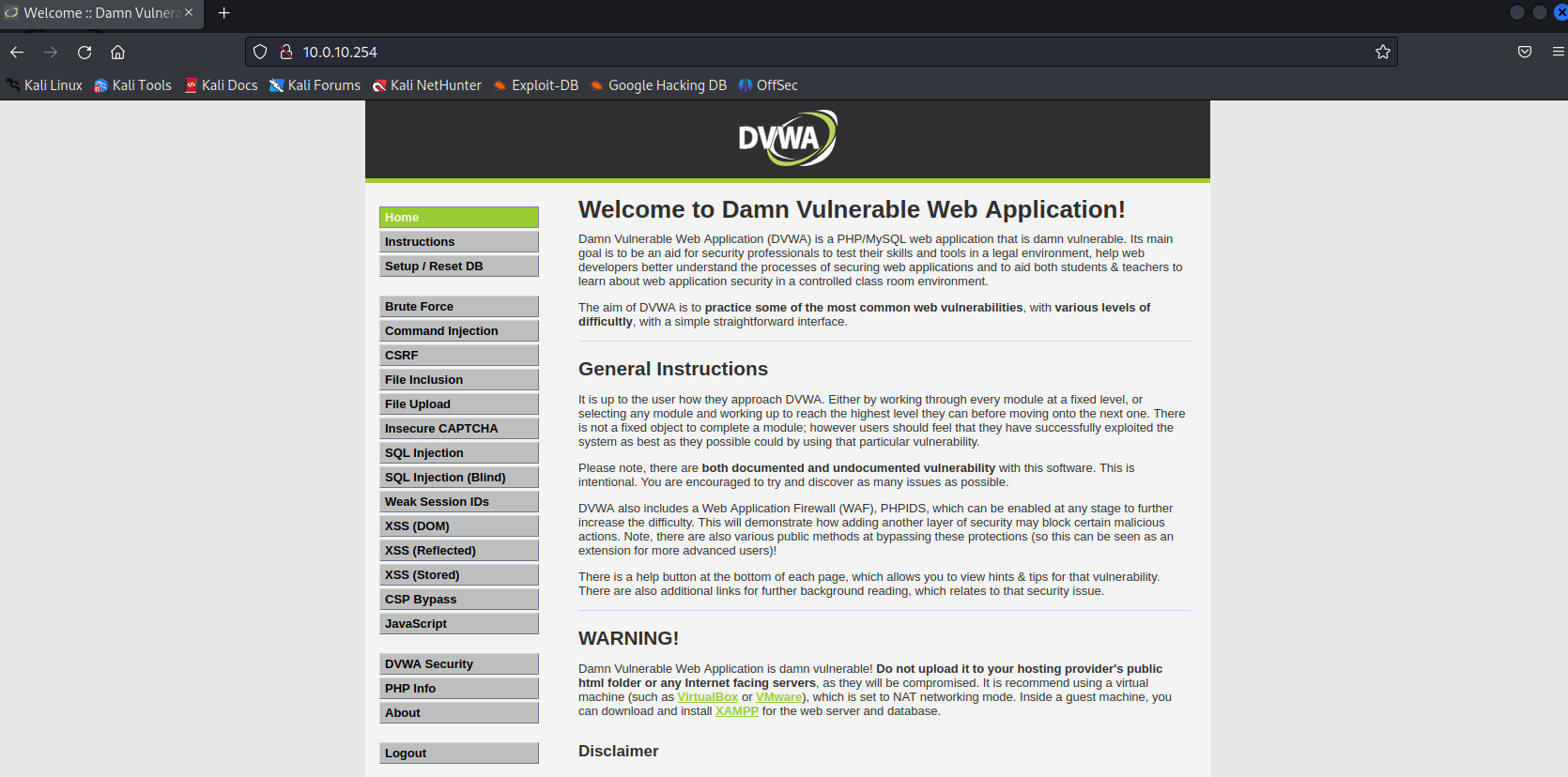
Try to open the website from the browser, by opening http://10.0.10.254. You should be able to see DVWA home page.
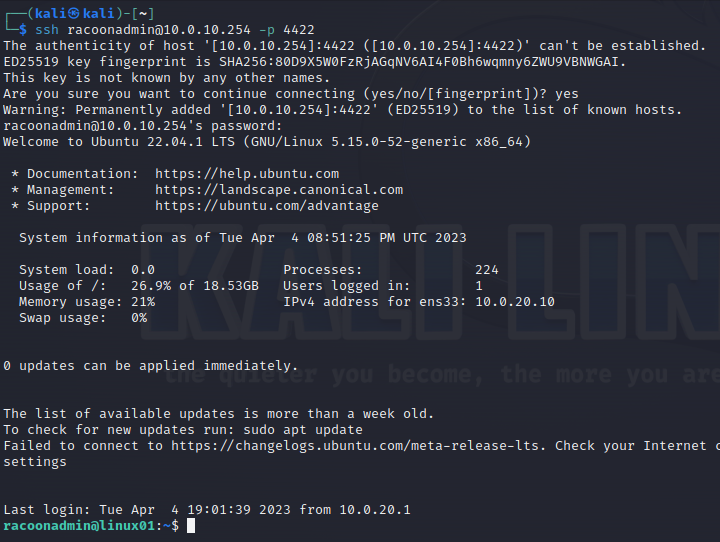
Now let’s try to SSH to the server (you can break the command before entering credentials).
And for the end, we can test MariaDB connection.
Summary
That is all for today. Now we have a prepared malicious machine for attacking our Racoon network and testing internal defense systems. At some point I will maybe add additional tools that will be used for attacking the network, but only if I don’t find a suitable one among the default Kali Linux tools. Next time we will (finally) start with deploying the SIEM and we will use Security Onion as a solution. Till the next time.